Cloud Security
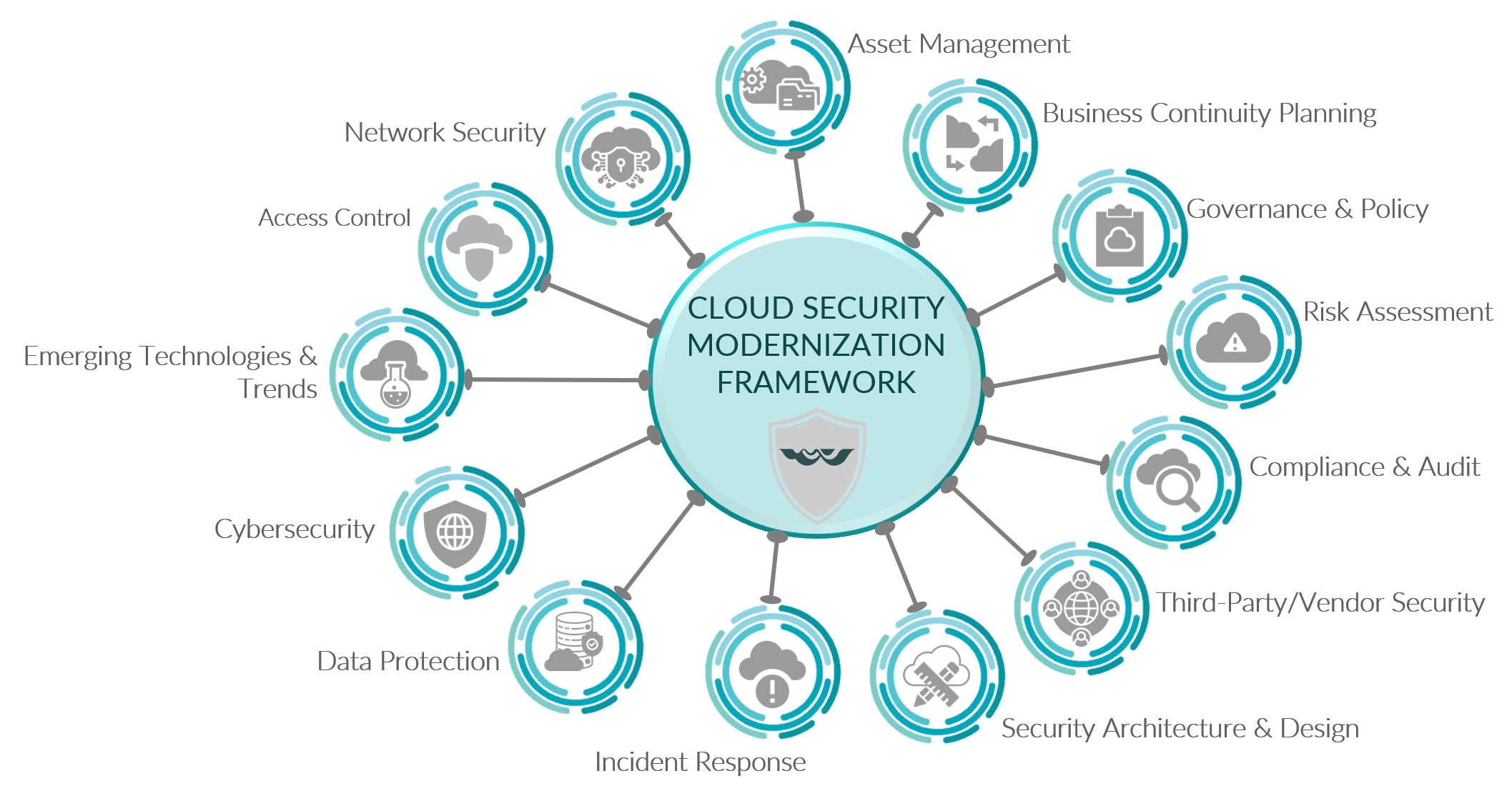
Cloud Security Modernization FrameworK
Asperitas Cloud Security Modernization Framework provides the structure to ensure that all areas of security are addressed in your cloud environment. The following areas are addressed within the framework.